2018 Updated Cisco 350-018 Security Written Exam Questions Online 1-10
In order to pass the Cisco Certification 350-018 exam, many Cisco Certified 350-018 testers spend a lot of time and effort, or spend a lot of money to attend remedial school. Pass4itsure contains questions and answers, similar to real-life questions. This can really be called the best Cisco 350-018 dump CCIE Security online issue. Cisco Certified 350-018 exams are a test of their expertise. Pass4itsure is a website that can help you quickly pass the Cisco Certified https://www.pass4itsure.com/350-018.html dumps staging test.
Question No : 1 Refer to the exhibit.
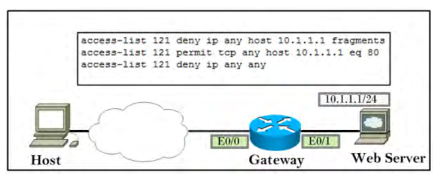
Identify the behavior of the ACL if it is applied inbound on E0/0.
A. The ACL will drop both initial and noninitial fragments for port 80 only.
B. The ACL will pass both initial and noninitial fragments for port 80 only.
C. The ACL will pass the initial fragment for port 80 but drop the noninitial fragment for any port.
D. The ACL will drop the initial fragment for port 80 but pass the noninitial fragment for any port.
Answer: C
Question No : 2
Which two statements about the IPv6 OSPFv3 authentication Trailer are true (choose two)
A. The AT-bit resides in the OSPFv3 Header field
B. The IPv6 Payload length includes the length of the authentication Trailer
C. It Provide an alternative option to OSPFv3 IPsec authentication
D. The AT-bit must be set only in OSPFv3 Hello packets that include an Authentication Trailer
E. The AT-bit must be set only in OSPFv3 Database Description packets that include an Authentication Trailer
F. The OSPFv3 packet length includes the length of the Authentication Trailer
Answer: D,E
Question No : 3
Which signature engine is used to create a custom IPS signature on a Cisco IPS appliance that triggers when a vulnerable web application identified by the “/runscript.php” URI is run?
A. AIC HTTP
B. Service HTTP
C. String TCP
D. Atomic IP
E. META
F. Multi-String
Answer: B
Question No : 4
Which three statements about NetFlow version 9 are correct? (Choose three.)
A. It is backward-compatible with versions 8 and 5.
B. Version 9 is dependent on the underlying transport; only UDP is supported.
C. A version 9 export packet consists of a packet header and flow sets.
D. Generating and maintaining valid template flow sets requires additional processing.
E. NetFlow version 9 does not access the NetFlow cache entry directly.
Answer: C,D,E
Question No : 5
Which port or ports are used for the FTP data channel in passive mode?
A. random TCP ports
B. TCP port 21 on the server side
C. TCP port 21 on the client side
D. TCP port 20 on the server side
E. TCP port 20 on the client side
Answer: A
Question No : 6
Which statement is true about an SNMPv2 communication?
A. The whole communication is not encrypted.
B. Only the community field is encrypted.
C. Only the query packets are encrypted.
D. The whole communication is encrypted.
Answer: A
Question No : 7
Refer to the exhibit.
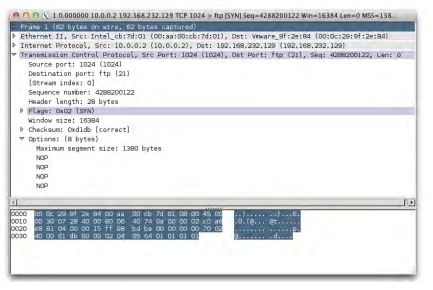
Which statement is true?
A. This packet decoder is using relative TCP sequence numbering?.
B. This TCP client is proposing the use of TCP window scaling?.
C. This packet represents an active FTP data session?.
D. This packet contains no TCP payload.
Answer: D
Question No : 8
What is the purpose of the BGP TTL security check?
A. The BGP TTL security check is used for iBGP session.
B. The BGP TTL security check protects against CPU utilization-based attacks.
C. The BGP TTL security check checks for a TTL value in packet header of less than or
equal to for successful peering.
D. The BGP TTL security check authenticates a peer.
E. The BGP TTL security check protects against routing table corruption.
Answer: B
Question No : 9 DRAG DROP
Drag and drop the components of a Teredo IPv6 packet from the left to the correct position
in the packet on the right

Answer:

Question No : 10 Which two statements about Network Edge Authentication Technology (NEAT) are true? (Choose two.)
A. It can be configured on both access ports and trunk ports.
B. It allows you to configure redundant links between authenticator and supplicant switches
C. It can be configured on both access ports and EtherChannel ports.
D. It supports port-based authentication on the authenticator switch.
E. It conflicts with auto-configuration
F. It requires a standard ACL on the switch port.
Answer: A,D
Pass4itsure can allow you to spend less time, money and effort to prepare for Cisco Certified 350-018 exams, which will provide you with the target Cisco 350-018 CCIE Security Online issues. You only need 20 hours of training to pass the exam successfully. If you are still trying to get through the 350-018 certification exam, pass4itsure can help you solve the problem. Pass4itsure can provide you with the good quality of Cisco 350-018 dumps CCIE Security Online issues to help you pass the exam, then you will become an excellent Cisco 350-018 certified member.
2016 Cisco 350-018 Dumps PDF Exam 1-20:
Exam A
QUESTION 1
In an L2TP voluntary tunneling scenario, the VPDN tunel is terminated between:
A. The client and the NAS.
B. The NAS and the LNS.
C. The NAS and the LAC.
D. The client and the LNS.
Correct Answer: D
QUESTION 2
Which IOS QoS mechanism is used strictly to rate limit traffic destined to the router itself?
A. Class-Based Policing
B. Control Plane Policing
C. Dual-Rate Policier
D. Single-Rate Policier.
Correct Answer: B
QUESTION 3
What are two key characteristics of VTP? (Choose 2)
A. VTP messages are sent out all switch-switch connections.
B. VTP L2 messages are communicated to neighbors using CDP.
C. VTP manages addition, deletion, and renaming of VLANs 1 to 4094.
D. VTP pruning restricts flooded traffic, increasing available bandwidth.
E. VTP V2 can only be used in a domain consisting of V2 capable switches.
F. VTP V2 performs consistency checks on all sources of VLAN information.
Correct Answer: DE
QUESTION 4
A network administrator is using a LAN analyzer to troubleshoot OSPF router exchange messages sent to ALL OSPF ROUTERS. To what MAC address are these messages sent?
A. 00-00-1C-EF-00-00
B. 01-00-5E-00-00-05
C. 01-00-5E-EF-00-00
D. EF-FF-FF-00-00-05
E. EF-00-00-FF-FF-FF
F. FF-FF-FF-FF-FF-FF
Correct Answer: B
QUESTION 5
Drop A.
B.
C.
D.
Correct Answer:
QUESTION 6
What is Chain of Evidence in the context of security forensics?
A. The concept that evidence is controlled in locked down, but not necessarily authenticated.
B. The concept that evidence is controlled and accounted for as to not disrupt its authenticity and integrity.
C. The concept that the general whereabouts of evidence is known.
D. The concept that if a person has possession of evidence someone knows where the evidence is and can say who had it if it is not logged
Correct Answer: B
QUESTION 7
In most buffer overflow attacks, which of the following behavior should be expected?
A. A vulnerability used to overflow the buffer and an exploit used to run malicious software off of the stack.
B. An exploit used to overflow the buffer and a vulnerability used to run malicious software off of the stack.
C. A single crafted packet to overflow the buffer and run malicious software.
D. Shell code to exploit the buffer.
Correct Answer: A
QUESTION 8
Which of the following is the most effective technique to prevent source IP Address spoofing?
A. policy based routing (PBR)
B. unicast reverse path forwarding (uRPF)
C. lock and key ACL
D. RFC 1918 filtering
E. IP source routing
Correct Answer: B
QUESTION 9
Whenever a failover takes place on the ASA (configured for failover), all active connections are dropped and clients must re-establish their connections unless:(Choose 2)
A. The ASA is configured for Active-Standby failover.
B. The ASA is configured for Active-Active failover.
C. The ASA is configured for Active-Active failover and a state failover link has been configured.
D. The ASA is configured for Active-Standby failover and a state failover link has been configured.
E. The ASA is configured to use a serial cable as failover link.
F. The ASA is configured for LAN-Based failover.
Correct Answer: CD
QUESTION 10
CSA protects your host by:
A. Preventing browsers from opening network sockets in listening state.
B. Preventing buffer overflows.
C. Preventing users from entering unencrypted passwords.
D. Preventing browsers from acting as client to web servers.
Correct Answer: A
QUESTION 11
Which three statements regarding Cisco ASA multicast routing support are correct? (Choose three.)
A. ASA supports both stub multicast routing and PIM multicast routing. However, you cannot configure both concurrently on a single security appliance.
B. When configured for stub multicast routing, the ASA can act as the Rendezvous Point (RP)
C. If the ASA detects IGMP version 1 routers, the ASA will automatically switch to IGMP version 1 operations.
D. The ASA supports both PIM-SM and bi-directional PIM.
E. Enabling multicast routing globally on the ASA automatically enables PIM and IGMP on all interfaces.
F. The ASA can be configured for IGMP snooping to constrain the flooding of multicast traffic by dynamically configuring the multicast traffic to be forwarded only those interfaces associated with hosts requesting the multicast group.
Correct Answer: ADE
QUESTION 12
Which of the following is true for RFC 4301 – Security Architecture for the Internet Protocol (obsoletes RFC 2401) – (Select two).
A. Specifies the Security Architecture for the Internet.
B. Specifies the base architecture for Key Management, the Internet Key Exchange (IKE)
C. Specifies the base architecture for IPsec-compliant systems.
D. Designed to provide security services for traffic at the IP layer, in the IPv4 environment only.
E. Designed to provide security services for traffic at the IP layer, in both the IPv4 and IPv6 environments
Correct Answer: CE
QUESTION 13
Which access control model provides access to system resources based on the job function of the user or the tasks that the user has been assigned?
A. Discretionary Access Control
B. Mandatory Access Control
C. Role Based Access Control
D. Context Based Access Control
E. Rule Based Access Control
Correct Answer: C
QUESTION 14
What does qos pre-classify provides in regard to implementing QoS over GRE/IPSec VPN tunnels?
A. enables IOS to copy the ToS field from the inner (original) IP header to the outer tunel IP header.
B. enables IOS to make a copy of the inner (original) IP header and to run a QoS classification before encryption, based on fields in the inner IP header.
C. enables IOS to classify packets based on the ToS field in the inner (original) IP header.
D. enables IOS to classify packets based on the ToS field in the outer tunnel IP header.
E. enables the IOS classification engine to only see a single encrypted and tunneled flow to reduce classification complexity.
Correct Answer: B
QUESTION 15
Which two steps does a receiver perform to validate a message using HMAC? (Choose two.)
A. decrypts the received MAC using a secret key.
B. compares the computed MAC vs. the MAC received.
C. authenticate the received message using the sender’s public key.
D. look up the sender’s public key.
E. extracts the MAC from the received message then encrypts the received message with a secret key to produce the MAC
F. Computes the MAC using the received message and a secret key as inputs to the hash function.
Correct Answer: BF
QUESTION 16
Refer to network diagram in the exhibit. There are four servers on the DMZ. All servers are capable of supporting both FTP and HTTP applications. When a remote user accesses the security appliance and is authenticated, according to the group configuration in the ny_acs server, a remote user from this group is authorized to perform what two actions? (Choose 2)
A. Access any server on the DMZ.
B. Access any FTP server on the DMZ.
C. Access “SVR 2” only
D. Utilize FTP and HTTP protocols
E. Utilize HTTP only
F. Utilize FTP only
Correct Answer: CF
QUESTION 17
Referring to the debug output shown below, what is causing the IKE Main Mode failure?
1d00h: ISAKMP (0:1): atts are not acceptable. Next payload is 0 1d00h: ISAKMP (0:1): no offers accepted!
1d00h: ISAKMP (0:1): SA not acceptable!
1d00h: %CRYPTO-6-IKMP_MODE_FAILURE: Processing of Main Mode failed with peer at 150.150.150.1
A. The IPSec transform set on the peers do not match.
B. The Crypto ACL is not a mirror image of the peer.
C. The pre-shared keys on the peers do not match.
D. The IKE Phase I policy does not match on both sides.
E. The received IPsec packet specifies a Security Parameters Index (SPI) that does not exist in the security associations database (SADB).
Correct Answer: D QUESTION 18
With the following GRE tunnel configuration, how many bytes of GRE overhead does encapsulation add to the original data packet?
interface Tunnel0 ip address 1.1.1.1 255.255.255.252 tunnel source Ethernet0/0 tunnel destination 2.2.2.2 tunnel key 1234
A. 20 bytes
B. 24 bytes
C. 28 bytes
D. 32 bytes
Correct Answer: C
QUESTION 19
With NetFlow configured and several IPS, switches, routers and firewall devices imported into its database, CS-MARS will provide which of the following security features? (Choose 4)
A. Event correlation to help identify attacks
B. Identification of hosts that generate abnormal amounts of traffic.
C. Identify which hosts have CSA installed.
D. Make mitigation recommendations to stop attacks.
E. Draw a topology of yout network.
F. Pull SNMP traps from different devices.
Correct answer: ABDE
Question 20
which RFC is usually used to protect your network when using IP Source address spoofing to enforce IP Source address spoofing and defeating denial of service attacks?
A. RFC 1149
B. RFC 3704
C. RFC 1918
D. RFC 2827
correct answer: D

