We provide good 200-201 dumps learning materials to help you study and pass the Cisco CBROPS 200-201 exam. You will have solid study material to prepare for the 200-201 (CBROPS) exam.
Pass4itSure has updated the new 200-201 dumps to provide you with valid 200-201 exam questions and answers, practice carefully, and you will pass the exam with ease. In the Pass4itSure 200-201 dumps webpage https://www.pass4itsure.com/200-201.html you’ll immediately get a brand new dumps quiz 264+.

Practice 200-201 Questions PDF Free [Drive]: https://drive.google.com/file/d/1KskgeVJ8CARohY0v5jWtsBvhzO0vub1U/view?usp=share_link to help you study and pass 200-201 exam!
What is the 200-201 (CBROPS) exam like?
The Cisco 200-201 exam costs $300. The exam, which consists of 95-105 questions, takes 120 minutes to complete. Successful passing of the exam earns the Cisco Certified CyberOps Associate.
Are there effective resources to prepare for the Cisco 200-201 exam?
- Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- CBROPS training videos
- CBROPS study materials
- Pass4itSure 200-201 dumps
How can I effectively prepare for the Cisco 200-201 exam?
- First, you need to know the details of the exam.
- Second, use the Pass4itSure website to get the latest 200-201 dumps learning materials.
- Finally, practice a lot, gain real practical experience, and increase your chances of success on the exam.
Where are the free 200-201 exam resources available?
The examrap.com blog is for you, and right below, you’ll find free Cisco 200-201 exam practice questions.
New! Cisco Free 200-201 Dumps Q&A
NEW QUESTION 1
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
A. detection and analysis
B. post-incident activity
C. vulnerability management
D. risk assessment
E. vulnerability scoring
Correct Answer: AB
Reference: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
NEW QUESTION 2
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet
inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
A. management and reporting
B. traffic filtering
C. adaptive AVC
D. metrics collection and exporting
E. application recognition
Correct Answer: AE
NEW QUESTION 3
What causes events on a Windows system to show Event Code 4625 in the log messages?
A. The system detected an XSS attack
B. Someone is trying a brute force attack on the network
C. Another device is gaining root access to the system
D. A privileged user successfully logged into the system
Correct Answer: B
NEW QUESTION 4
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions. Which
Does the identifier track an active program?
A. application identification number
B. active process identification number
C. runtime identification number
D. process identification number
Correct Answer: D
NEW QUESTION 5
Refer to the exhibit.

An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An
engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo
report?
A. Win32.polip.a.exe is an executable file and should be flagged as malicious.
B. The file is clean and does not represent a risk.
C. Cuckoo cleaned the malicious file and prepared it for usage.
D. MD5 of the file was not identified as malicious.
Correct Answer: C
NEW QUESTION 6
What should an engineer use to aid the trusted exchange of public keys between user tom0411976943 and
dan1968754032?
A. central key management server
B. web of trust
C. trusted certificate authorities
D. registration authority data
Correct Answer: C
NEW QUESTION 7
What describes the concept of data consistently and readily accessible for legitimate users?
A. integrity
B. availability
C. accessibility
D. confidentiality
Correct Answer: B
NEW QUESTION 8
Refer to the exhibit.

What is shown in this PCAP file?
A. Timestamps are indicated with errors.
B. The protocol is TCP.
C. The User-Agent is Mozilla/5.0.
D. The HTTP GET is encoded.
Correct Answer: D
NEW QUESTION 9
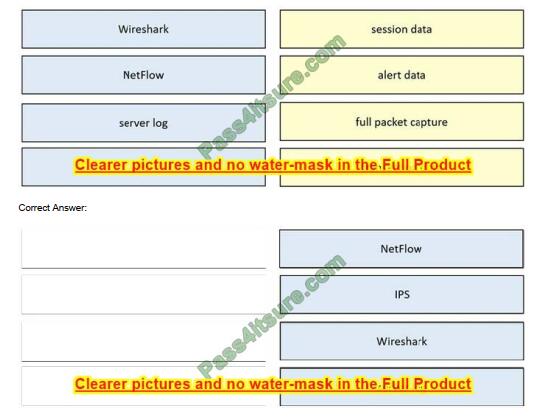
DRAG DROP
Drag and drop the data source from the left onto the data type on the right.
Select and Place:
NEW QUESTION 10
A system administrator is ensuring that specific registry information is accurate. Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
A. file extension associations
B. hardware, software, and security settings for the system
C. currently logged-in users, including folders and control panel settings
D. all users on the system, including visual settings
Correct Answer: B
NEW QUESTION 11
How does a certificate authority impact security?
A. It validates client identity when communicating with the server.
B. It authenticates client identity when requesting an SSL certificate.
C. It authenticates domain identity when requesting an SSL certificate.
D. It validates the domain identity of the SSL certificate.
Correct Answer: D
A certificate authority is a computer or entity that creates and issues digital certificates. CA does not “authenticate” it
validates. “D” is wrong because The digital certificate validates a user. CA –> DC –> user, server, or whatever.
Reference: https://en.wikipedia.org/wiki/Certificate_authority
NEW QUESTION 12
An analyst is exploring the functionality of different operating systems. What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
A. queries Linux devices that have Microsoft Services for Linux installed
B. deploys Windows Operating Systems in an automated fashion
C. is an efficient tool for working with Active Directory
D. has a Common Information Model, which describes installed hardware and software
Correct Answer: D
NEW QUESTION 13
What is the difference between data obtained from Tap and SPAN ports?
A. Tap mirrors existing traffic from specified ports, while SPAN presents more structured data for deeper analysis.
B. SPAN passively splits traffic between a network device and the network without altering it, while Tap alters the response times.
C. SPAN improves the detection of media errors, while Tap provides direct access to traffic with lowered data visibility.
D. Tap sends traffic from physical layers to the monitoring device, while SPAN provides a copy of network traffic from
switch to destination
Correct Answer: D
Reference: https://www.gigamon.com/resources/resource-library/white-paper/to-tap-or-to-span.html
If you prepare diligently, you can pass the 200-201 exam with a high score. Especially with the 200-201 dumps help. Download the Pass4itSure 200-201 dumps here: https://www.pass4itsure.com/200-201.html
So start now and get ready for a successful career!
